
With a Core emphasis on cybersecurity and ICT infrastructure for Small, Medium and Micro Enterprises, COREX’s Service division caters to various needs, providing essential services such as data backup, device management, ransomware detection, and disaster recovery. Moreover, we take pride in pioneering a unique offering for the country – AI GPU server resources rental and marketplace, empowering small startups and students to delve into AI development without exorbitant expenditure. At COREX, our mission is to bridge the technological gap and make cutting-edge solutions accessible to all.
Cloud & Infrastructure

Next Generation Firewall

Internet Access Gateway
Backup & Disaster Recovery

Device Management

Cyber Security
SOLUTIONS
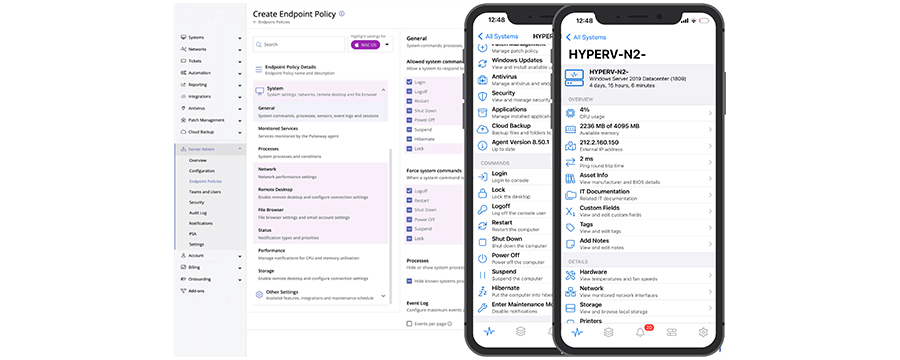
Our COREX device manager service offers a comprehensive range of solutions to effectively manage your devices. With our expertise, you can expect the following benefits:
- Networking Monitoring: We provide continuous monitoring of your network to ensure its stability and optimal performance.
- Patch Management: Our service covers both operating system and third-party software patch management, ensuring that your devices are up to date and protected against vulnerabilities.
- IT Automation: We streamline your IT operations through automation, allowing you to reduce manual tasks and improve overall efficiency.
- Active Directory Management: We take care of your Active Directory infrastructure, ensuring proper user management, security, and authentication.
- Server Monitoring: Our service includes monitoring the health and performance of your servers, identifying issues proactively, and minimizing downtime.
- Mobile Monitoring App: We offer a mobile monitoring application that enables you to keep track of your devices and receive notifications on the go.
Server Monitoring and Management Software
Link our software to a single server, enabling access to all servers within the Database Availability Group (DAG). Get notified about database mount and dismount events, exercise control over replication queues, and establish limits. Experience reassurance as you efficiently manage mailboxes, proactively preventing potential issues from affecting users.
Key Features:
- Receive Critical Server Health Alerts
- Monitor Mailboxes
- Track Queues
- Observe Database Status
- Manage Transport Settings
- Perform One-Tap Health Test
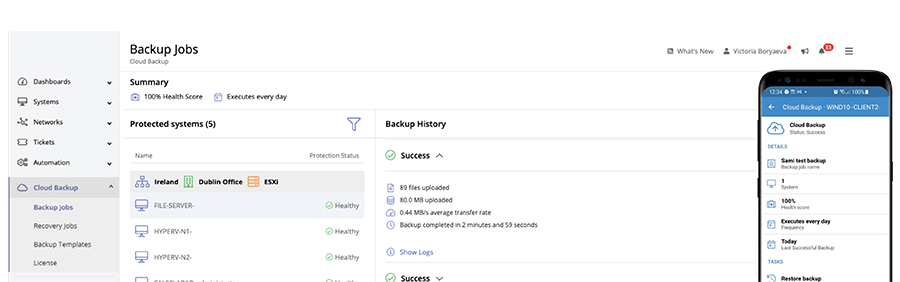
Our backup and disaster recovery service provides you with reliable data protection and recovery solutions. By leveraging our expertise, you can mitigate the risk of data loss and ensure business continuity in the event of a disaster.
Within the application, you have the ability to:
- Swiftly deploy backup agents
- Handle backup and recovery tasks
- Monitor backup status
- Effortlessly include backup tasks in your daily workflow
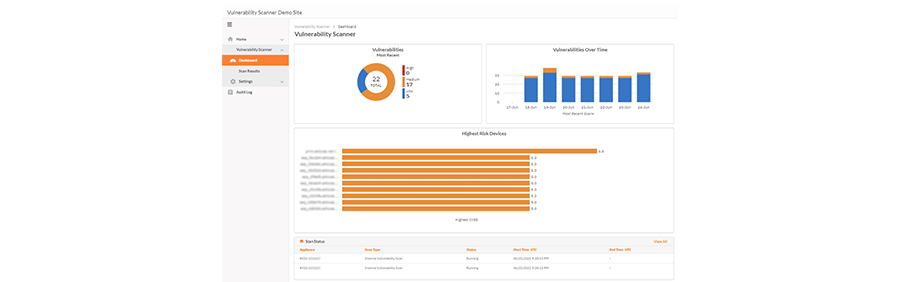
Our Ransomware Detection feature provides an extra level of real-time security by autonomously identifying suspicious file behaviors commonly associated with potential ransomware threats. Apart from notifying you about suspicious file activity, it can also automatically terminate the process, isolate, or even shut down the suspected device, enabling you to conduct further investigation. Even in isolated mode, you can still connect to any device through the RMM.
Our services include:
- Automated Ransomware Detection
- Phishing Protection
- Security Awareness Training
- Patch Management
- Vulnerability Scanning
Prevent data loss and downtime caused by ransomware using our integrated detection, immutability safeguards, and automated recovery capabilities that ensure swift restoration after an attack. In today’s landscape, data exists in numerous locations and faces continuous threats. Among the crucial defenses against ransomware, backups play a pivotal role. The time is ripe to develop your ransomware recovery strategy and attain cyber resilience.

We offer AI GPU server resources rental and a marketplace where you can access high-performance computing capabilities for your artificial intelligence workloads. Our servers are optimized for AI processing, enabling you to accelerate your research and development projects.
Product Features:
- Platform Import: Help the team manage GPU resources more effectively. Offer IT managers and AI developers a machine learning development and operation platform with a user-friendly web interface. This platform allows for greater flexibility and efficiency in utilizing GPU resources, enabling users to fully harness the GPU computing power whenever needed.
- In-depth AI development: Seamlessly connect with commonly used AI development tools
- Resource Isolation: Authority management and quota limit. The administrator has the authority to oversee user permissions for both tenants (groups) and individual accounts. By setting usage quotas, they can prevent resource abuse and ensure effective allocation of resources among users.
- Automated Execution: Pre-set single or batch inference. The user has the flexibility to configure inference tasks, which can be executed on-demand or set as task templates for batch processing. By pre-setting the execution time, the system can complete the tasks as required, even during off-duty hours, ensuring seamless execution anytime and anywhere.
Supporting integrated hardware systems, unified management, and multiple container-shared GPU mechanisms allows for efficient sharing of GPU resources among multiple users and containers, facilitating AI development and accommodating multiple AI computing nodes simultaneously. The platform also provides a feature-rich web visualization interface that offers real-time and historical views of CPU, memory, network, GPU, GPU temperature, node count, execution status, usage status, available capacity, and device load status.
While containers are running, users can monitor the real-time usage status of various resources like CPU, memory, network, and GPU. Additionally, the system automatically triggers email alarms when computing resources are extensively used, reminding managers to stay attentive to available resource slots. This functionality aids managers in rational allocation and efficient management of computing resources.
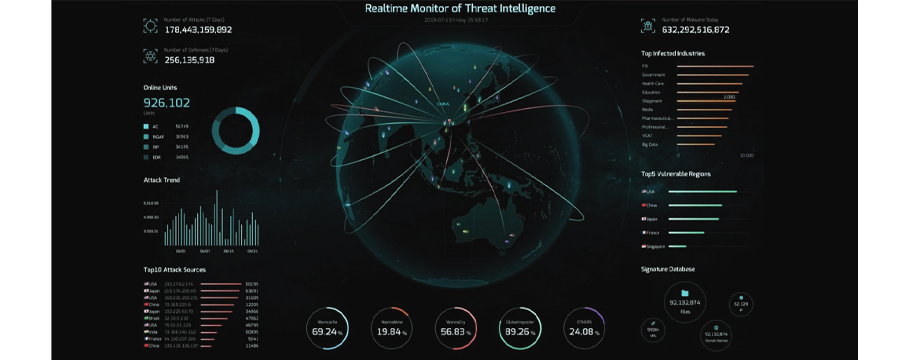
Our comprehensive cyber security services encompass various solutions to protect your digital assets and mitigate risks. The following are some of the services we provide:
- Next-Generation Firewall (NGAF): We deploy advanced firewalls to secure your network from threats and unauthorized access.
- Cyber Command: Our cyber command service helps you establish a robust security framework, including policies, procedures, and incident response plans. It offers superior threat detection and response capabilities by closely monitoring internal network traffic. By utilizing AI and behavior analysis technology, it correlates existing security events with global threat intelligence, bolstering your defense against threats. Cyber command uncovers any security breaches that may have occurred and performs impact analysis to identify hidden threats within your network. The platform also seamlessly integrates network and endpoint security solutions, allowing for automated and simplified responses to potential threats.
- Endpoint Secure: We ensure the security of your endpoints, such as laptops, desktops, and mobile devices, through advanced threat detection and prevention mechanisms. Endpoint security offers passive detection with Signature-based Dectection (Traditional AV), Behavior-based Detection (NG-AV), AI & Machine Learning (NG-AV) and Sandboxing (NG-AV). Active Protection offers: Micro-segmentation, Ransomware Honeypot, Two-factor Authentication and Brute-force Attack Detection.
- IAG (Identity and Access Governance): Our IAG service helps you manage user identities, access rights, and permissions to prevent unauthorized access and data breaches.
- Application Containment: We implement application containment strategies to isolate and protect critical applications from potential threats.
- Anti-Ransomware: Our anti-ransomware solutions help you defend against ransomware attacks and recover encrypted data.
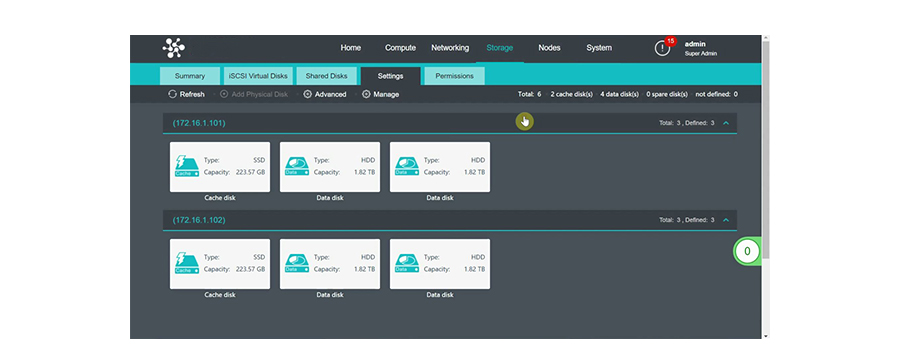
Our cloud and infrastructure services provide scalable and reliable solutions to support your digital transformation journey. We offer the following services:
- HCI (Hyperconverged Infrastructure): We design and implement hyperconverged infrastructure solutions that combine compute, storage, and networking resources to simplify management and enhance agility.
- ADesk (Virtual Desktop Infrastructure):
Introducing our Virtual Desktop Infrastructure (VDI) solution, designed to smoothly transition your business into a digital workspace environment, catering to secure office setups, work-from-anywhere scenarios, and beyond.
Its remarkably simple architecture empowers IT engineers of all expertise levels to manage with ease, leading to a substantial increase in IT operations and maintenance efficiency. With self-developed transmission protocols and cutting-edge GPU technology in collaboration with Nvidia, we ensure a seamless desktop experience that enhances user productivity.
Moreover, our VDI solution incorporates end-to-end security mechanisms, safeguarding your data from external threats such as ransomware, internal data leaks, and data loss due to disk errors. It comprehensively addresses business security and compliance requirements, ensuring a safe and protected work environment.
- SD-WAN (Software-Defined Wide Area Networking): We deploy software-defined networking solutions to optimize your wide area network connectivity, enhance performance, and reduce costs.
- PAAS (Platform as a Service): Introducing our PaaS solution, meticulously crafted to provide customers with a user-friendly enterprise-grade platform. This cutting-edge platform facilitates the storage, execution, and management of containerized workloads for businesses. PaaS optimizes the entire process of developing and operating containerized applications, ensuring a streamlined and efficient experience on our platform.
Contact us today to learn more about our COREX services and how they can help your business thrive in the digital era.

